General updates
WAF Release - 2025-07-21 - Emergency
This week's update highlights several high-impact vulnerabilities affecting Microsoft SharePoint Server. These flaws, involving unsafe deserialization, allow unauthenticated remote code execution over the network, posing a critical threat to enterprise environments relying on SharePoint for collaboration and document management.
Key Findings
- Microsoft SharePoint Server (CVE-2025-53770): A critical vulnerability involving unsafe deserialization of untrusted data, enabling unauthenticated remote code execution over the network. This flaw allows attackers to execute arbitrary code on vulnerable SharePoint servers without user interaction.
- Microsoft SharePoint Server (CVE-2025-53771): A closely related deserialization issue that can be exploited by unauthenticated attackers, potentially leading to full system compromise. The vulnerability highlights continued risks around insecure serialization logic in enterprise collaboration platforms.
Impact
Together, these vulnerabilities significantly weaken the security posture of on-premise Microsoft SharePoint Server deployments. By enabling remote code execution without authentication, they open the door for attackers to gain persistent access, deploy malware, and move laterally across enterprise environments.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100817 | Microsoft SharePoint - Deserialization - CVE:CVE-2025-53770 | N/A | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100818 | Microsoft SharePoint - Deserialization - CVE:CVE-2025-53771 | N/A | Block | This is a New Detection |
For more details, also refer to our blog ↗.
WAF Release - 2025-07-21
This week's update spotlights several critical vulnerabilities across Citrix NetScaler Memory Disclosure, FTP servers and network application. Several flaws enable unauthenticated remote code execution or sensitive data exposure, posing a significant risk to enterprise security.
Key Findings
- Wing FTP Server (CVE-2025-47812): A critical Remote Code Execution (RCE) vulnerability that enables unauthenticated attackers to execute arbitrary code with root/SYSTEM-level privileges by exploiting a Lua injection flaw.
- Infoblox NetMRI (CVE-2025-32813): A remote unauthenticated command injection flaw that allows an attacker to execute arbitrary commands, potentially leading to unauthorized access.
- Citrix Netscaler ADC (CVE-2025-5777, CVE-2023-4966): A sensitive information disclosure vulnerability, also known as "Citrix Bleed2", that allows the disclosure of memory and subsequent remote access session hijacking.
- Akamai CloudTest (CVE-2025-49493): An XML External Entity (XXE) injection that could lead to read local files on the system by manipulating XML input.
Impact
These vulnerabilities affect critical enterprise infrastructure, from file transfer services and network management appliances to application delivery controllers. The Wing FTP RCE and Infoblox command injection flaws offer direct paths to deep system compromise, while the Citrix "Bleed2" and Akamai XXE vulnerabilities undermine system integrity by enabling session hijacking and sensitive data theft.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100804 | BerriAI - SSRF - CVE:CVE-2024-6587 | Log | Log | This is a New Detection | |
| Cloudflare Managed Ruleset | 100805 | Wing FTP Server - Remote Code Execution - CVE:CVE-2025-47812 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100807 | Infoblox NetMRI - Command Injection - CVE:CVE-2025-32813 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100808 | Citrix Netscaler ADC - Buffer Error - CVE:CVE-2025-5777 | Log | Disabled | This is a New Detection | |
| Cloudflare Managed Ruleset | 100809 | Citrix Netscaler ADC - Information Disclosure - CVE:CVE-2023-4966 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100810 | Akamai CloudTest - XXE - CVE:CVE-2025-49493 | Log | Block | This is a New Detection |
WAF Release - 2025-07-14
This week’s vulnerability analysis highlights emerging web application threats that exploit modern JavaScript behavior and SQL parsing ambiguities. Attackers continue to refine techniques such as attribute overloading and obfuscated logic manipulation to evade detection and compromise front-end and back-end systems.
Key Findings
- XSS – Attribute Overloading: A novel cross-site scripting technique where attackers abuse custom or non-standard HTML attributes to smuggle payloads into the DOM. These payloads evade traditional sanitization logic, especially in frameworks that loosely validate attributes or trust unknown tokens.
- XSS – onToggle Event Abuse: Exploits the lesser-used onToggle event (triggered by elements like
<details>) to execute arbitrary JavaScript when users interact with UI elements. This vector is often overlooked by static analyzers and can be embedded in seemingly benign components. - SQLi – Obfuscated Boolean Logic: An advanced SQL injection variant that uses non-standard Boolean expressions, comment-based obfuscation, or alternate encodings (for example,
/*!true*/,AND/**/1=1) to bypass basic input validation and WAF signatures. This technique is particularly dangerous in dynamic query construction contexts.
Impact
These vulnerabilities target both user-facing components and back-end databases, introducing potential vectors for credential theft, session hijacking, or full data exfiltration. The XSS variants bypass conventional filters through overlooked HTML behaviors, while the obfuscated SQLi enables attackers to stealthily probe back-end logic, making them especially difficult to detect and block.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100798 | XSS - Attribute Overloading | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100799 | XSS - OnToggle | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100800 | SQLi - Obfuscated Boolean | Log | Block | This is a New Detection |
Increased IP List Limits for Enterprise Accounts
We have significantly increased the limits for IP Lists on Enterprise plans to provide greater flexibility and control:
- Total number of lists: Increased from 10 to 1,000.
- Total number of list items: Increased from 10,000 to 500,000.
Limits for other list types and plans remain unchanged. For more details, refer to the lists availability.
WAF Release - 2025-07-07
This week’s roundup uncovers critical vulnerabilities affecting enterprise VoIP systems, webmail platforms, and a popular JavaScript framework. The risks range from authentication bypass to remote code execution (RCE) and buffer handling flaws, each offering attackers a path to elevate access or fully compromise systems.
Key Findings
- Next.js - Auth Bypass: A newly detected authentication bypass flaw in the Next.js framework allows attackers to access protected routes or APIs without proper authorization, undermining application access controls.
- Fortinet FortiVoice (CVE-2025-32756): A buffer error vulnerability in FortiVoice systems that could lead to memory corruption and potential code execution or service disruption in enterprise telephony environments.
- Roundcube (CVE-2025-49113): A critical RCE flaw allowing unauthenticated attackers to execute arbitrary PHP code via crafted requests, leading to full compromise of mail servers and user inboxes.
Impact
These vulnerabilities affect core business infrastructure, from web interfaces to voice communications and email platforms. The Roundcube RCE and FortiVoice buffer flaw offer potential for deep system access, while the Next.js auth bypass undermines trust boundaries in modern web apps.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100795 | Next.js - Auth Bypass | Log | Disabled | This is a New Detection | |
| Cloudflare Managed Ruleset | 100796 | Fortinet FortiVoice - Buffer Error - CVE:CVE-2025-32756 | Log | Disabled | This is a New Detection | |
| Cloudflare Managed Ruleset | 100797 | Roundcube - Remote Code Execution - CVE:CVE-2025-49113 | Log | Disabled | This is a New Detection |
WAF Release - 2025-06-16
This week’s roundup highlights multiple critical vulnerabilities across popular web frameworks, plugins, and enterprise platforms. The focus lies on remote code execution (RCE), server-side request forgery (SSRF), and insecure file upload vectors that enable full system compromise or data exfiltration.
Key Findings
- Cisco IOS XE (CVE-2025-20188): Critical RCE vulnerability enabling unauthenticated attackers to execute arbitrary commands on network infrastructure devices, risking total router compromise.
- Axios (CVE-2024-39338): SSRF flaw impacting server-side request control, allowing attackers to manipulate internal service requests when misconfigured with unsanitized user input.
- vBulletin (CVE-2025-48827, CVE-2025-48828): Two high-impact RCE flaws enabling attackers to remotely execute PHP code, compromising forum installations and underlying web servers.
- Invision Community (CVE-2025-47916): A critical RCE vulnerability allowing authenticated attackers to run arbitrary code in community platforms, threatening data and lateral movement risk.
- CrushFTP (CVE-2025-32102, CVE-2025-32103): SSRF vulnerabilities in upload endpoint processing permit attackers to pivot internal network scans and abuse internal services.
- Roundcube (CVE-2025-49113): RCE via email processing enables attackers to execute code upon viewing a crafted email — particularly dangerous for webmail deployments.
- WooCommerce WordPress Plugin (CVE-2025-47577): Dangerous file upload vulnerability permits unauthenticated users to upload executable payloads, leading to full WordPress site takeover.
- Cross-Site Scripting (XSS) Detection Improvements: Enhanced detection patterns.
Impact
These vulnerabilities span core systems — from routers to e-commerce to email. RCE in Cisco IOS XE, Roundcube, and vBulletin poses full system compromise. SSRF in Axios and CrushFTP supports internal pivoting, while WooCommerce’s file upload bug opens doors to mass WordPress exploitation.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100783 | Cisco IOS XE - Remote Code Execution - CVE:CVE-2025-20188 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100784 | Axios - SSRF - CVE:CVE-2024-39338 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100785 | vBulletin - Remote Code Execution - CVE:CVE-2025-48827, CVE:CVE-2025-48828 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100786 | Invision Community - Remote Code Execution - CVE:CVE-2025-47916 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100791 | CrushFTP - SSRF - CVE:CVE-2025-32102, CVE:CVE-2025-32103 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100792 | Roundcube - Remote Code Execution - CVE:CVE-2025-49113 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100793 | XSS - Ontoggle | Log | Disabled | This is a New Detection | |
| Cloudflare Managed Ruleset | 100794 | WordPress WooCommerce Plugin - Dangerous File Upload - CVE:CVE-2025-47577 | Log | Block | This is a New Detection |
WAF Release - 2025-06-09
This week’s update spotlights four critical vulnerabilities across CMS platforms, VoIP systems, and enterprise applications. Several flaws enable remote code execution or privilege escalation, posing significant enterprise risks.
Key Findings
- WordPress OttoKit Plugin (CVE-2025-27007): Privilege escalation flaw allows unauthenticated attackers to create or elevate user accounts, compromising WordPress administrative control.
- SAP NetWeaver (CVE-2025-42999): Remote Code Execution vulnerability enables attackers to execute arbitrary code on SAP NetWeaver systems, threatening core ERP and business operations.
- Fortinet FortiVoice (CVE-2025-32756): Buffer error vulnerability may lead to memory corruption and potential code execution, directly impacting enterprise VoIP infrastructure.
- Camaleon CMS (CVE-2024-46986): Remote Code Execution vulnerability allows attackers to gain full control over Camaleon CMS installations, exposing hosted content and underlying servers.
Impact
These vulnerabilities target widely deployed CMS, ERP, and VoIP systems. RCE flaws in SAP NetWeaver and Camaleon CMS allow full takeover of business-critical applications. Privilege escalation in OttoKit exposes WordPress environments to full administrative compromise. FortiVoice buffer handling issues risk destabilizing or fully compromising enterprise telephony systems.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100769 | WordPress OttoKit Plugin - Privilege Escalation - CVE:CVE-2025-27007 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100770 | SAP NetWeaver - Remote Code Execution - CVE:CVE-2025-42999 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100779 | Fortinet FortiVoice - Buffer Error - CVE:CVE-2025-32756 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100780 | Camaleon CMS - Remote Code Execution - CVE:CVE-2024-46986 | Log | Block | This is a New Detection |
WAF Release - 2025-06-02
This week’s roundup highlights five high-risk vulnerabilities affecting SD-WAN, load balancers, and AI platforms. Several flaws enable unauthenticated remote code execution or authentication bypass.
Key Findings
- Versa Concerto SD-WAN (CVE-2025-34026, CVE-2025-34027): Authentication bypass vulnerabilities allow attackers to gain unauthorized access to SD-WAN management interfaces, compromising network segmentation and control.
- Kemp LoadMaster (CVE-2024-7591): Remote Code Execution vulnerability enables attackers to execute arbitrary commands, potentially leading to full device compromise within enterprise load balancing environments.
- AnythingLLM (CVE-2024-0759): Server-Side Request Forgery (SSRF) flaw allows external attackers to force the LLM backend to make unauthorized internal network requests, potentially exposing sensitive internal resources.
- Anyscale Ray (CVE-2023-48022): Remote Code Execution vulnerability affecting distributed AI workloads, allowing attackers to execute arbitrary code on Ray cluster nodes.
- Server-Side Request Forgery (SSRF) - Generic & Obfuscated Payloads: Ongoing advancements in SSRF payload techniques observed, including obfuscation and expanded targeting of cloud metadata services and internal IP ranges.
Impact
These vulnerabilities expose critical infrastructure across networking, AI platforms, and SaaS integrations. Unauthenticated RCE and auth bypass flaws in Versa Concerto, Kemp LoadMaster, and Anyscale Ray allow full system compromise. AnythingLLM and SSRF payload variants expand attack surfaces into internal cloud resources, sensitive APIs, and metadata services, increasing risk of privilege escalation, data theft, and persistent access.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100764 | Versa Concerto SD-WAN - Auth Bypass - CVE:CVE-2025-34027 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100765 | Versa Concerto SD-WAN - Auth Bypass - CVE:CVE-2025-34026 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100766 | Kemp LoadMaster - Remote Code Execution - CVE:CVE-2024-7591 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100767 | AnythingLLM - SSRF - CVE:CVE-2024-0759 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100768 | Anyscale Ray - Remote Code Execution - CVE:CVE-2023-48022 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100781 | SSRF - Generic Payloads | N/A | Disabled | This is a New Detection | |
| Cloudflare Managed Ruleset | 100782 | SSRF - Obfuscated Payloads | N/A | Disabled | This is a New Detection |
Updated attack score model
We have deployed an updated attack score model focused on enhancing the detection of multiple false positives (FPs).
As a result of this improvement, some changes in observed attack scores are expected.
WAF Release - 2025-05-27
This week’s roundup covers nine vulnerabilities, including six critical RCEs and one dangerous file upload. Affected platforms span cloud services, CI/CD pipelines, CMSs, and enterprise backup systems. Several are now addressed by updated WAF managed rulesets.
Key Findings
- Ingress-Nginx (CVE-2025-1098): Unauthenticated RCE via unsafe annotation handling. Impacts Kubernetes clusters.
- GitHub Actions (CVE-2025-30066): RCE through malicious workflow inputs. Targets CI/CD pipelines.
- Craft CMS (CVE-2025-32432): Template injection enables unauthenticated RCE. High risk to content-heavy sites.
- F5 BIG-IP (CVE-2025-31644): RCE via TMUI exploit, allowing full system compromise.
- AJ-Report (CVE-2024-15077): RCE through untrusted template execution. Affects reporting dashboards.
- NAKIVO Backup (CVE-2024-48248): RCE via insecure script injection. High-value target for ransomware.
- SAP NetWeaver (CVE-2025-31324): Dangerous file upload flaw enables remote shell deployment.
- Ivanti EPMM (CVE-2025-4428, 4427): Auth bypass allows full access to mobile device management.
- Vercel (CVE-2025-32421): Information leak via misconfigured APIs. Useful for attacker recon.
Impact
These vulnerabilities expose critical components across Kubernetes, CI/CD pipelines, and enterprise systems to severe threats including unauthenticated remote code execution, authentication bypass, and information leaks. High-impact flaws in Ingress-Nginx, Craft CMS, F5 BIG-IP, and NAKIVO Backup enable full system compromise, while SAP NetWeaver and AJ-Report allow remote shell deployment and template-based attacks. Ivanti EPMM’s auth bypass further risks unauthorized control over mobile device fleets.
GitHub Actions and Vercel introduce supply chain and reconnaissance risks, allowing malicious workflow inputs and data exposure that aid in targeted exploitation. Organizations should prioritize immediate patching, enhance monitoring, and deploy updated WAF and IDS signatures to defend against likely active exploitation.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100746 | Vercel - Information Disclosure | Log | Disabled | This is a New Detection | |
| Cloudflare Managed Ruleset | 100754 | AJ-Report - Remote Code Execution - CVE:CVE-2024-15077 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100756 | NAKIVO Backup - Remote Code Execution - CVE:CVE-2024-48248 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100757 | Ingress-Nginx - Remote Code Execution - CVE:CVE-2025-1098 | Log | Disabled | This is a New Detection | |
| Cloudflare Managed Ruleset | 100759 | SAP NetWeaver - Dangerous File Upload - CVE:CVE-2025-31324 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100760 | Craft CMS - Remote Code Execution - CVE:CVE-2025-32432 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100761 | GitHub Action - Remote Code Execution - CVE:CVE-2025-30066 | Log | Disabled | This is a New Detection | |
| Cloudflare Managed Ruleset | 100762 | Ivanti EPMM - Auth Bypass - CVE:CVE-2025-4428, CVE:CVE-2025-4427 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100763 | F5 Big IP - Remote Code Execution - CVE:CVE-2025-31644 | Log | Disabled | This is a New Detection |
WAF Release - 2025-05-19
This week's analysis covers four vulnerabilities, with three rated critical due to their Remote Code Execution (RCE) potential. One targets a high-traffic frontend platform, while another targets a popular content management system. These detections are now part of the Cloudflare Managed Ruleset in Block mode.
Key Findings
- Commvault Command Center (CVE-2025-34028) exposes an unauthenticated RCE via insecure command injection paths in the web UI. This is critical due to its use in enterprise backup environments.
- BentoML (CVE-2025-27520) reveals an exploitable vector where serialized payloads in model deployment APIs can lead to arbitrary command execution. This targets modern AI/ML infrastructure.
- Craft CMS (CVE-2024-56145) allows RCE through template injection in unauthenticated endpoints. It poses a significant risk for content-heavy websites with plugin extensions.
- Apache HTTP Server (CVE-2024-38475) discloses sensitive server config data due to misconfigured
mod_proxybehavior. While not RCE, this is useful for pre-attack recon.
Impact
These newly detected vulnerabilities introduce critical risk across modern web stacks, AI infrastructure, and content platforms: unauthenticated RCEs in Commvault, BentoML, and Craft CMS enable full system compromise with minimal attacker effort.
Apache HTTPD information leak can support targeted reconnaissance, increasing the success rate of follow-up exploits. Organizations using these platforms should prioritize patching and monitor for indicators of exploitation using updated WAF detection rules.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100745 | Apache HTTP Server - Information Disclosure - CVE:CVE-2024-38475 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100747 | Commvault Command Center - Remote Code Execution - CVE:CVE-2025-34028 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100749 | BentoML - Remote Code Execution - CVE:CVE-2025-27520 | Log | Disabled | This is a New Detection | |
| Cloudflare Managed Ruleset | 100753 | Craft CMS - Remote Code Execution - CVE:CVE-2024-56145 | Log | Block | This is a New Detection |
Improved Payload Logging for WAF Managed Rules
We have upgraded WAF Payload Logging to enhance rule diagnostics and usability:
- Targeted logging: Logs now capture only the specific portions of requests that triggered WAF rules, rather than entire request segments.
- Visual highlighting: Matched content is visually highlighted in the UI for faster identification.
- Enhanced context: Logs now include surrounding context to make diagnostics more effective.
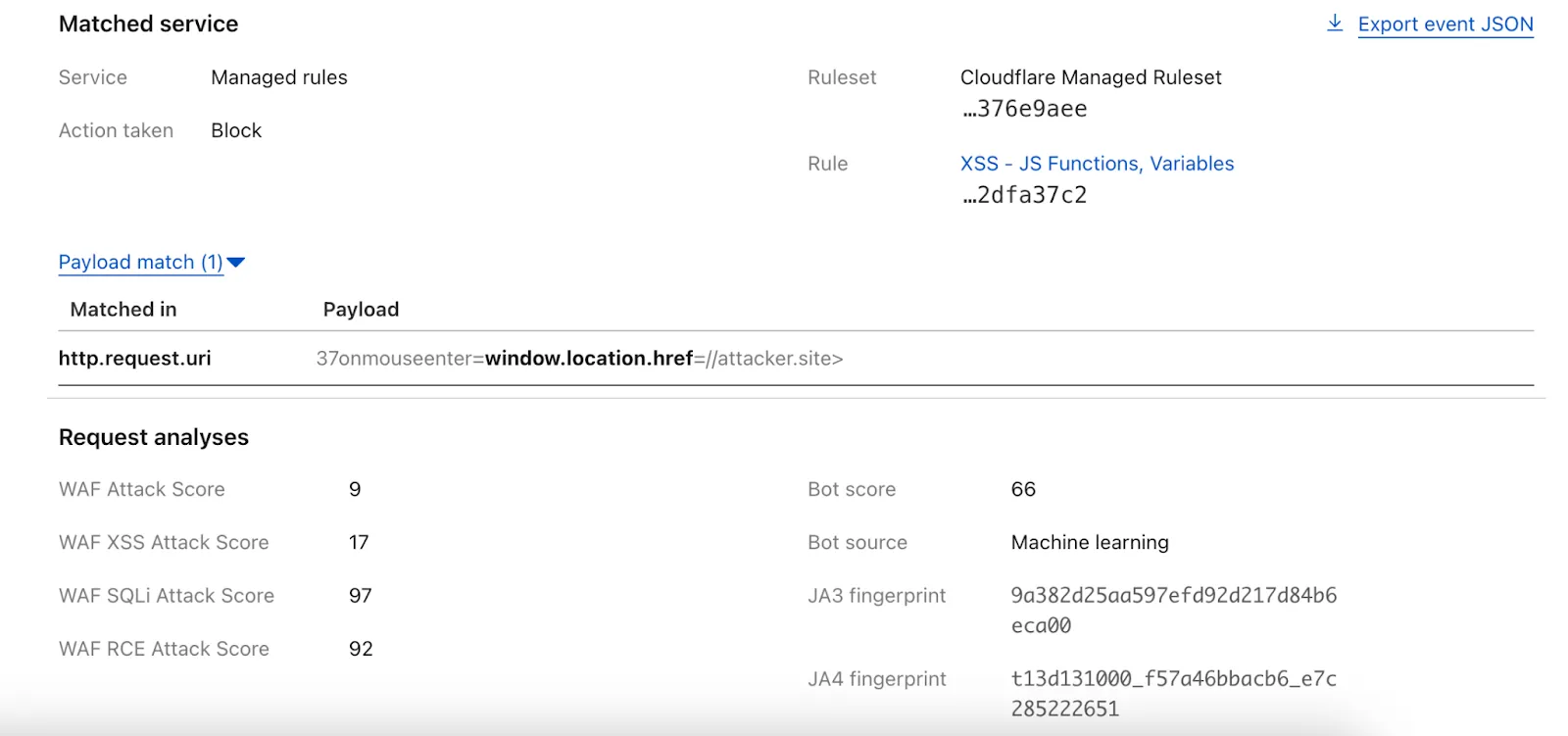
Payload Logging is available to all Enterprise customers. If you have not used Payload Logging before, check how you can get started.
Note: The structure of the encrypted_matched_data field in Logpush has changed from Map<Field, Value> to Map<Field, {Before: bytes, Content: Value, After: bytes}>. If you rely on this field in your Logpush jobs, you should review and update your processing logic accordingly.
WAF Release - 2025-05-05
This week's analysis covers five CVEs with varying impact levels. Four are rated critical, while one is rated high severity. Remote Code Execution vulnerabilities dominate this set.
Key Findings
GFI KerioControl (CVE-2024-52875) contains an unauthenticated Remote Code Execution (RCE) vulnerability that targets firewall appliances. This vulnerability can let attackers gain root level system access, making this CVE particularly attractive for threat actors.
The SonicWall SMA vulnerabilities remain concerning due to their continued exploitation since 2021. These critical vulnerabilities in remote access solutions create dangerous entry points to networks.
Impact
Customers using the Managed Ruleset will receive rule coverage following this week's release. Below is a breakdown of the recommended prioritization based on current exploitation trends:
- GFI KerioControl (CVE-2024-52875) - Highest priority; unauthenticated RCE
- SonicWall SMA (Multiple vulnerabilities) - Critical for network appliances
- XWiki (CVE-2025-24893) - High priority for development environments
- Langflow (CVE-2025-3248) - Important for AI workflow platforms
- MinIO (CVE-2025-31489) - Important for object storage implementations
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100724 | GFI KerioControl - Remote Code Execution - CVE:CVE-2024-52875 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100748 | XWiki - Remote Code Execution - CVE:CVE-2025-24893 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100750 | SonicWall SMA - Dangerous File Upload - CVE:CVE-2021-20040, CVE:CVE-2021-20041, CVE:CVE-2021-20042 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100751 | Langflow - Remote Code Execution - CVE:CVE-2025-3248 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100752 | MinIO - Auth Bypass - CVE:CVE-2025-31489 | Log | Block | This is a New Detection |
WAF Release - 2025-04-26 - Emergency
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100755 | React.js - Router and Remix Vulnerability - CVE:CVE-2025-43864, CVE:CVE-2025-43865 | Block | Block | This is a New Detection |
WAF Release - 2025-04-22
Each of this week's rule releases covers a distinct CVE, with half of the rules targeting Remote Code Execution (RCE) attacks. Of the 6 CVEs covered, four were scored as critical, with the other two scored as high.
When deciding which exploits to tackle, Cloudflare tunes into the attackers' areas of focus. Cloudflare's network intelligence provides a unique lens into attacker activity – for instance, through the volume of blocked requests related with CVE exploits after updating WAF Managed Rules with new detections.
From this week's releases, one indicator that RCE is a "hot topic" attack type is the fact that the Oracle PeopleSoft RCE rule accounts for half of all of the new rule matches. This rule patches CVE-2023-22047, a high-severity vulnerability in the Oracle PeopleSoft suite that allows unauthenticated attackers to access PeopleSoft Enterprise PeopleTools data through remote code execution. This is particularly concerning because of the nature of the data managed by PeopleSoft – this can include payroll records or student profile information. This CVE, along with five others, are addressed with the latest detection update to WAF Managed Rules.
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100738 | GitLab - Auth Bypass - CVE:CVE-2023-7028 | Log | Disabled | This is a New Detection | |
| Cloudflare Managed Ruleset | 100740 | Splunk Enterprise - Remote Code Execution - CVE:CVE-2025-20229 | Log | Disabled | This is a New Detection | |
| Cloudflare Managed Ruleset | 100741 | Oracle PeopleSoft - Remote Code Execution - CVE:CVE-2023-22047 | Log | Disabled | This is a New Detection | |
| Cloudflare Managed Ruleset | 100742 | CrushFTP - Auth Bypass - CVE:CVE-2025-31161 | Log | Disabled | This is a New Detection | |
| Cloudflare Managed Ruleset | 100743 | Ivanti - Buffer Error - CVE:CVE-2025-22457 | Log | Disabled | This is a New Detection | |
| Cloudflare Managed Ruleset | 100744 | Oracle Access Manager - Remote Code Execution - CVE:CVE-2021-35587 | Log | Disabled | This is a New Detection |
WAF Release - 2025-04-14
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100739A | Next.js - Auth Bypass - CVE:CVE-2025-29927 - 2 | Log | Disabled | This is a New Detection |
WAF Release - 2025-04-02
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100732 | Sitecore - Code Injection - CVE:CVE-2025-27218 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100733 | Angular-Base64-Upload - Remote Code Execution - CVE:CVE-2024-42640 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100734 | Apache Camel - Remote Code Execution - CVE:CVE-2025-29891 | Log | Disabled | This is a New Detection | |
| Cloudflare Managed Ruleset | 100735 | Progress Software WhatsUp Gold - Remote Code Execution - CVE:CVE-2024-4885 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100737 | Apache Tomcat - Remote Code Execution - CVE:CVE-2025-24813 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100659 | Common Payloads for Server-side Template Injection | N/A | Disabled | N/A | |
| Cloudflare Managed Ruleset | 100659 | Common Payloads for Server-side Template Injection - Base64 | N/A | Disabled | N/A | |
| Cloudflare Managed Ruleset | 100642 | LDAP Injection | N/A | Disabled | N/A | |
| Cloudflare Managed Ruleset | 100642 | LDAP Injection Base64 | N/A | Disabled | N/A | |
| Cloudflare Managed Ruleset | 100005 | DotNetNuke - File Inclusion - CVE:CVE-2018-9126, CVE:CVE-2011-1892, CVE:CVE-2022-31474 | N/A | Disabled | N/A | |
| Cloudflare Managed Ruleset | 100527 | Apache Struts - CVE:CVE-2021-31805 | N/A | Block | N/A | |
| Cloudflare Managed Ruleset | 100702 | Command Injection - CVE:CVE-2022-24108 | N/A | Block | N/A | |
| Cloudflare Managed Ruleset | 100622C | Ivanti - Command Injection - CVE:CVE-2023-46805, CVE:CVE-2024-21887, CVE:CVE-2024-22024 | N/A | Block | N/A | |
| Cloudflare Managed Ruleset | 100536C | GraphQL Command Injection | N/A | Disabled | N/A | |
| Cloudflare Managed Ruleset | 100536 | GraphQL Injection | N/A | Disabled | N/A | |
| Cloudflare Managed Ruleset | 100536A | GraphQL Introspection | N/A | Disabled | N/A | |
| Cloudflare Managed Ruleset | 100536B | GraphQL SSRF | N/A | Disabled | N/A | |
| Cloudflare Managed Ruleset | 100559A | Prototype Pollution - Common Payloads | N/A | Disabled | N/A | |
| Cloudflare Managed Ruleset | 100559A | Prototype Pollution - Common Payloads - Base64 | N/A | Disabled | N/A | |
| Cloudflare Managed Ruleset | 100734 | Apache Camel - Remote Code Execution - CVE:CVE-2025-29891 | N/A | Disabled | N/A |
WAF Release - 2025-03-22 - Emergency
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100739 | Next.js - Auth Bypass - CVE:CVE-2025-29927 | N/A | Disabled | This is a New Detection |
New Managed WAF rule for Next.js CVE-2025-29927.
Update: Mon Mar 24th, 11PM UTC: Next.js has made further changes to address a smaller vulnerability introduced in the patches made to its middleware handling. Users should upgrade to Next.js versions 15.2.4, 14.2.26, 13.5.10 or 12.3.6. If you are unable to immediately upgrade or are running an older version of Next.js, you can enable the WAF rule described in this changelog as a mitigation.
Update: Mon Mar 24th, 8PM UTC: Next.js has now backported the patch for this vulnerability ↗ to cover Next.js v12 and v13. Users on those versions will need to patch to 13.5.9 and 12.3.5 (respectively) to mitigate the vulnerability.
Update: Sat Mar 22nd, 4PM UTC: We have changed this WAF rule to opt-in only, as sites that use auth middleware with third-party auth vendors were observing failing requests.
We strongly recommend updating your version of Next.js (if eligible) to the patched versions, as your app will otherwise be vulnerable to an authentication bypass attack regardless of auth provider.
This rule is opt-in only for sites on the Pro plan or above in the WAF managed ruleset.
To enable the rule:
- Head to Security > WAF > Managed rules in the Cloudflare dashboard for the zone (website) you want to protect.
- Click the three dots next to Cloudflare Managed Ruleset and choose Edit
- Scroll down and choose Browse Rules
- Search for CVE-2025-29927 (ruleId:
34583778093748cc83ff7b38f472013e) - Change the Status to Enabled and the Action to Block. You can optionally set the rule to Log, to validate potential impact before enabling it. Log will not block requests.
- Click Next
- Scroll down and choose Save
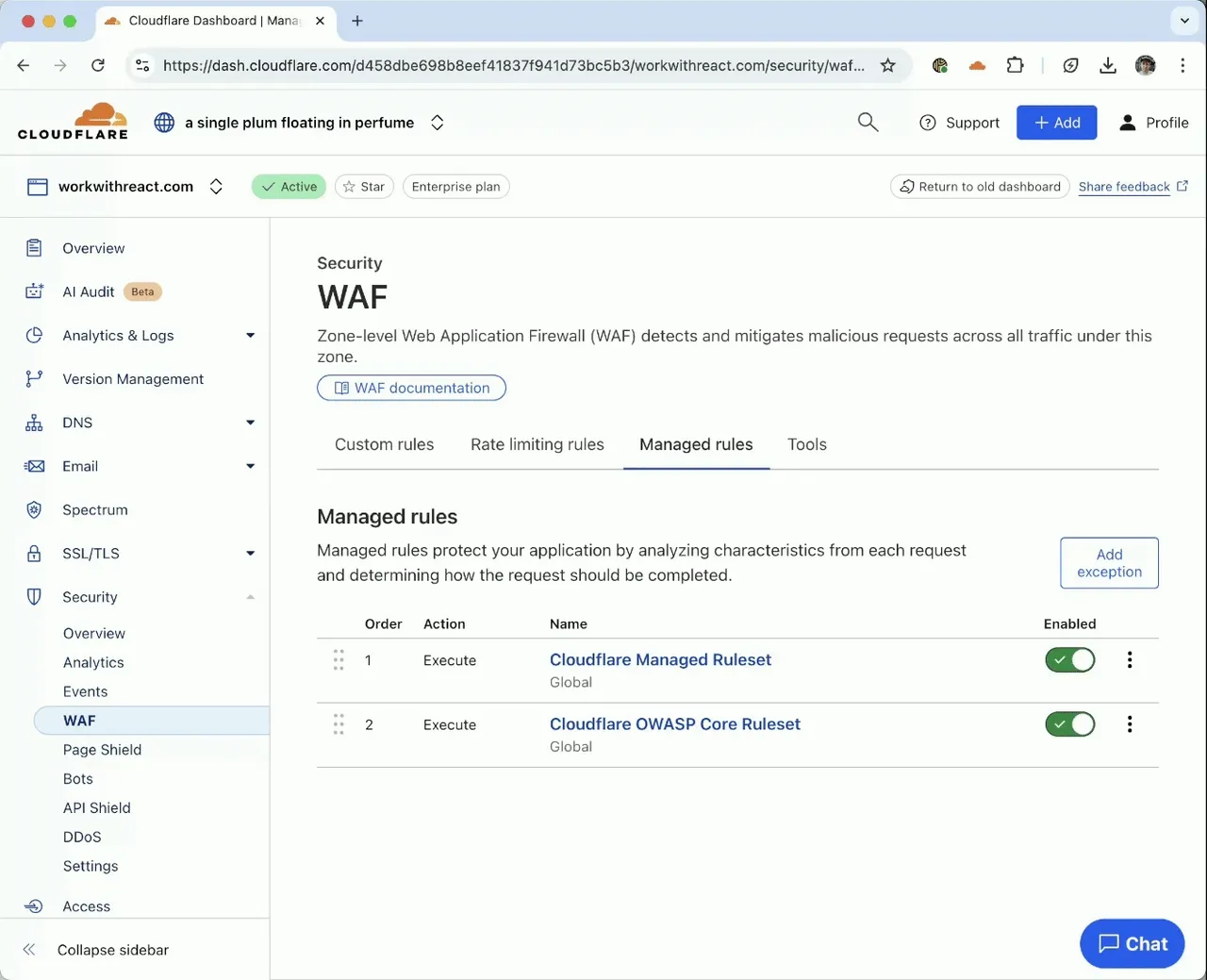
This will enable the WAF rule and block requests with the x-middleware-subrequest header regardless of Next.js version.
For users on the Free plan, or who want to define a more specific rule, you can create a Custom WAF rule to block requests with the x-middleware-subrequest header regardless of Next.js version.
To create a custom rule:
- Head to Security > WAF > Custom rules in the Cloudflare dashboard for the zone (website) you want to protect.
- Give the rule a name - e.g.
next-js-CVE-2025-29927 - Set the matching parameters for the rule match any request where the
x-middleware-subrequestheaderexistsper the rule expression below.
(len(http.request.headers["x-middleware-subrequest"]) > 0)- Set the action to 'block'. If you want to observe the impact before blocking requests, set the action to 'log' (and edit the rule later).
- Deploy the rule.
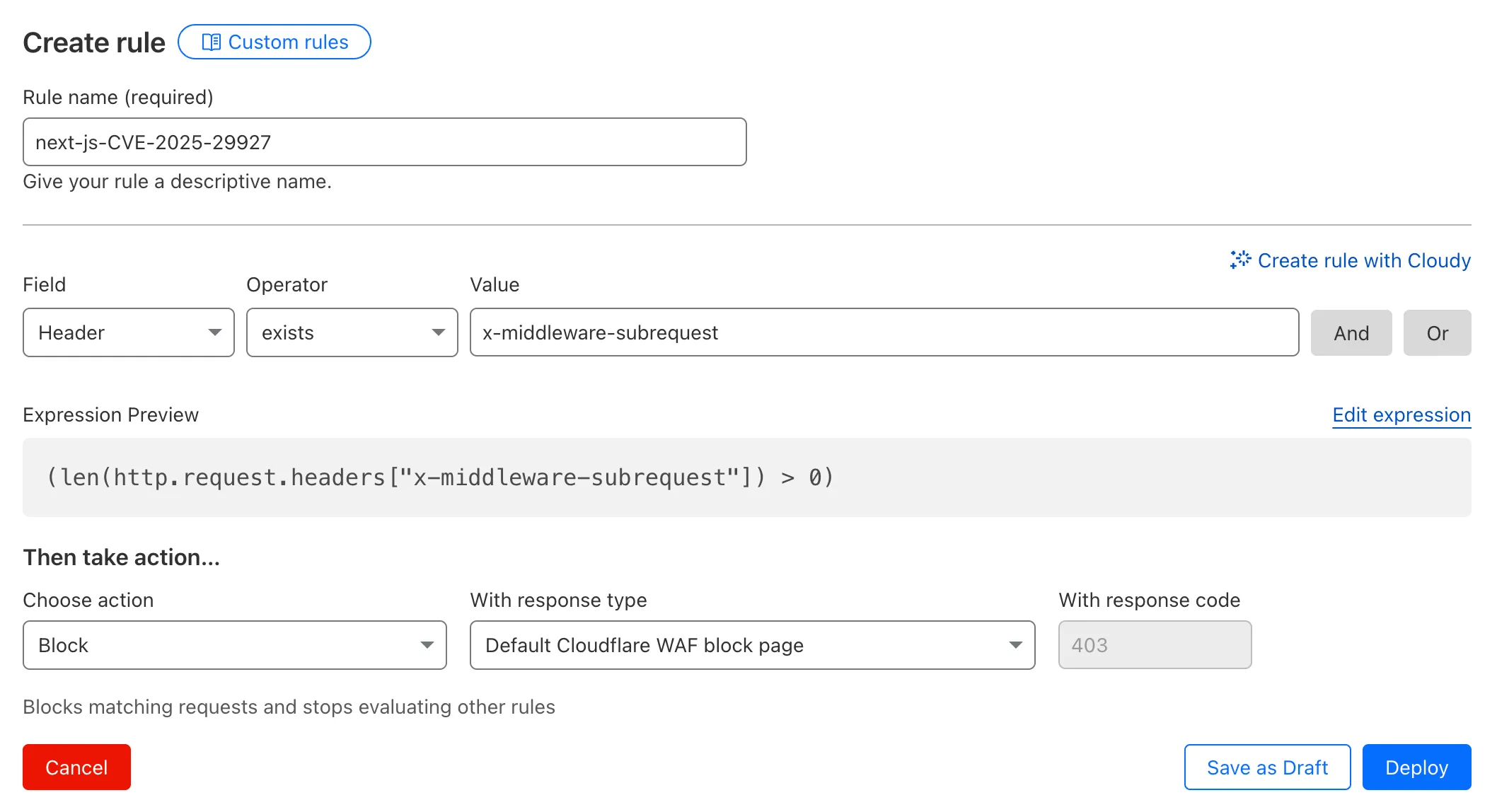
We've made a WAF (Web Application Firewall) rule available to all sites on Cloudflare to protect against the Next.js authentication bypass vulnerability ↗ (CVE-2025-29927) published on March 21st, 2025.
Note: This rule is not enabled by default as it blocked requests across sites for specific authentication middleware.
- This managed rule protects sites using Next.js on Workers and Pages, as well as sites using Cloudflare to protect Next.js applications hosted elsewhere.
- This rule has been made available (but not enabled by default) to all sites as part of our WAF Managed Ruleset and blocks requests that attempt to bypass authentication in Next.js applications.
- The vulnerability affects almost all Next.js versions, and has been fully patched in Next.js
14.2.26and15.2.4. Earlier, interim releases did not fully patch this vulnerability. - Users on older versions of Next.js (
11.1.4to13.5.6) did not originally have a patch available, but this the patch for this vulnerability and a subsequent additional patch have been backported to Next.js versions12.3.6and13.5.10as of Monday, March 24th. Users on Next.js v11 will need to deploy the stated workaround or enable the WAF rule.
The managed WAF rule mitigates this by blocking external user requests with the x-middleware-subrequest header regardless of Next.js version, but we recommend users using Next.js 14 and 15 upgrade to the patched versions of Next.js as an additional mitigation.
WAF Release - 2025-03-19 - Emergency
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100736 | Generic HTTP Request Smuggling | N/A | Disabled | This is a New Detection |
WAF Release - 2025-03-17
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100725 | Fortinet FortiManager - Remote Code Execution - CVE:CVE-2023-42791, CVE:CVE-2024-23666 | Log | Block | ||
| Cloudflare Managed Ruleset | 100726 | Ivanti - Remote Code Execution - CVE:CVE-2024-8190 | Log | Block | ||
| Cloudflare Managed Ruleset | 100727 | Cisco IOS XE - Remote Code Execution - CVE:CVE-2023-20198 | Log | Block | ||
| Cloudflare Managed Ruleset | 100728 | Sitecore - Remote Code Execution - CVE:CVE-2024-46938 | Log | Block | ||
| Cloudflare Managed Ruleset | 100729 | Microsoft SharePoint - Remote Code Execution - CVE:CVE-2023-33160 | Log | Block | ||
| Cloudflare Managed Ruleset | 100730 | Pentaho - Template Injection - CVE:CVE-2022-43769, CVE:CVE-2022-43939 | Log | Block | ||
| Cloudflare Managed Ruleset | 100700 | Apache SSRF vulnerability CVE-2021-40438 | N/A | Block |
WAF Release - 2025-03-11 - Emergency
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100731 | Apache Camel - Code Injection - CVE:CVE-2025-27636 | N/A | Block | This is a New Detection |
WAF Release - 2025-03-10
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100722 | Ivanti - Information Disclosure - CVE:CVE-2025-0282 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100723 | Cisco IOS XE - Information Disclosure - CVE:CVE-2023-20198 | Log | Block | This is a New Detection |
Updated leaked credentials database
Added new records to the leaked credentials database. The record sources are: Have I Been Pwned (HIBP) database, RockYou 2024 dataset, and another third-party database.
WAF Release - 2025-03-03
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100721 | Ivanti - Remote Code Execution - CVE:CVE-2024-13159, CVE:CVE-2024-13160, CVE:CVE-2024-13161 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100596 | Citrix Content Collaboration ShareFile - Remote Code Execution - CVE:CVE-2023-24489 | N/A | Block |
WAF Release - 2025-02-24
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100718A | SonicWall SSLVPN 2 - Auth Bypass - CVE:CVE-2024-53704 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100720 | Palo Alto Networks - Auth Bypass - CVE:CVE-2025-0108 | Log | Block | This is a New Detection |
WAF Release - 2025-02-18
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100715 | FortiOS - Auth Bypass - CVE:CVE-2024-55591 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100716 | Ivanti - Auth Bypass - CVE:CVE-2021-44529 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100717 | SimpleHelp - Auth Bypass - CVE:CVE-2024-57727 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100718 | SonicWall SSLVPN - Auth Bypass - CVE:CVE-2024-53704 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100719 | Yeti Platform - Auth Bypass - CVE:CVE-2024-46507 | Log | Block | This is a New Detection |
WAF Release - 2025-02-11
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100708 | Aviatrix Network - Remote Code Execution - CVE:CVE-2024-50603 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100709 | Next.js - Remote Code Execution - CVE:CVE-2024-46982 | Log | Disabled | This is a New Detection | |
| Cloudflare Managed Ruleset | 100710 | Progress Software WhatsUp Gold - Directory Traversal - CVE:CVE-2024-12105 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100711 | WordPress - Remote Code Execution - CVE:CVE-2024-56064 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100712 | WordPress - Remote Code Execution - CVE:CVE-2024-9047 | Log | Block | This is a New Detection | |
| Cloudflare Managed Ruleset | 100713 | FortiOS - Auth Bypass - CVE:CVE-2022-40684 | Log | Block | This is a New Detection |
Updated leaked credentials database
Added new records to the leaked credentials database from a third-party database.
WAF Release - 2025-01-21
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100303 | Command Injection - Nslookup | Log | Block | This was released as | |
| Cloudflare Managed Ruleset | 100534 | Web Shell Activity | Log | Block | This was released as |
WAF Release - 2025-01-13
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Managed Ruleset | 100704 | Cleo Harmony - Auth Bypass - CVE:CVE-2024-55956, CVE:CVE-2024-55953 | Log | Block | New Detection | |
| Cloudflare Managed Ruleset | 100705 | Sentry - SSRF | Log | Block | New Detection | |
| Cloudflare Managed Ruleset | 100706 | Apache Struts - Remote Code Execution - CVE:CVE-2024-53677 | Log | Block | New Detection | |
| Cloudflare Managed Ruleset | 100707 | FortiWLM - Remote Code Execution - CVE:CVE-2023-48782, CVE:CVE-2023-34993, CVE:CVE-2023-34990 | Log | Block | New Detection | |
| Cloudflare Managed Ruleset | 100007C_BETA | Command Injection - Common Attack Commands | Disabled |
WAF Release - 2025-01-06
| Ruleset | Rule ID | Legacy Rule ID | Description | Previous Action | New Action | Comments |
|---|---|---|---|---|---|---|
| Cloudflare Specials | 100678 | Pandora FMS - Remote Code Execution - CVE:CVE-2024-11320 | Log | Block | New Detection | |
| Cloudflare Specials | 100679 | Palo Alto Networks - Remote Code Execution - CVE:CVE-2024-0012, CVE:CVE-2024-9474 | Log | Block | New Detection | |
| Cloudflare Specials | 100680 | Ivanti - Command Injection - CVE:CVE-2024-37397 | Log | Block | New Detection | |
| Cloudflare Specials | 100681 | Really Simple Security - Auth Bypass - CVE:CVE-2024-10924 | Log | Block | New Detection | |
| Cloudflare Specials | 100682 | Magento - XXE - CVE:CVE-2024-34102 | Log | Block | New Detection | |
| Cloudflare Specials | 100683 | CyberPanel - Remote Code Execution - CVE:CVE-2024-51567 | Log | Block | New Detection | |
| Cloudflare Specials | 100684 | Microsoft SharePoint - Remote Code Execution - CVE:CVE-2024-38094, CVE:CVE-2024-38024, CVE:CVE-2024-38023 | Log | Block | New Detection | |
| Cloudflare Specials | 100685 | CyberPanel - Remote Code Execution - CVE:CVE-2024-51568 | Log | Block | New Detection | |
| Cloudflare Specials | 100686 | Seeyon - Remote Code Execution | Log | Block | New Detection | |
| Cloudflare Specials | 100687 | WordPress - Remote Code Execution - CVE:CVE-2024-10781, CVE:CVE-2024-10542 | Log | Block | New Detection | |
| Cloudflare Specials | 100688 | ProjectSend - Remote Code Execution - CVE:CVE-2024-11680 | Log | Block | New Detection | |
| Cloudflare Specials | 100689 | Palo Alto GlobalProtect - Remote Code Execution - CVE:CVE-2024-5921 | Log | Block | New Detection | |
| Cloudflare Specials | 100690 | Ivanti - Remote Code Execution - CVE:CVE-2024-37404 | Log | Block | New Detection | |
| Cloudflare Specials | 100691 | Array Networks - Remote Code Execution - CVE:CVE-2023-28461 | Log | Block | New Detection | |
| Cloudflare Specials | 100692 | CyberPanel - Remote Code Execution - CVE:CVE-2024-51378 | Log | Block | New Detection | |
| Cloudflare Specials | 100693 | Symfony Profiler - Auth Bypass - CVE:CVE-2024-50340 | Log | Block | New Detection | |
| Cloudflare Specials | 100694 | Citrix Virtual Apps - Remote Code Execution - CVE:CVE-2024-8069 | Log | Block | New Detection | |
| Cloudflare Specials | 100695 | MSMQ Service - Remote Code Execution - CVE:CVE-2023-21554 | Log | Block | New Detection | |
| Cloudflare Specials | 100696 | Nginxui - Remote Code Execution - CVE:CVE-2024-49368 | Log | Block | New Detection | |
| Cloudflare Specials | 100697 | Apache ShardingSphere - Remote Code Execution - CVE:CVE-2022-22733 | Log | Block | New Detection | |
| Cloudflare Specials | 100698 | Mitel MiCollab - Auth Bypass - CVE:CVE-2024-41713 | Log | Block | New Detection | |
| Cloudflare Specials | 100699 | Apache Solr - Auth Bypass - CVE:CVE-2024-45216 | Log | Block | New Detection |
Improved VPN Managed List
Customers can now effectively manage incoming traffic identified as originating from VPN IPs. Customers with compliance restrictions can now ensure compliance with local laws and regulations. Customers with CDN restrictions can use the improved VPN Managed List to prevent unauthorized access from users attempting to bypass geographical restrictions. With the new VPN Managed List enhancements, customers can improve their overall security posture to reduce exposure to unwanted or malicious traffic.
Change the order of list items in IP Lists (for API and Terraform users)
Due to changes in the API implementation, the order of list items in an IP list obtained via API or Terraform may change, which may cause Terraform to detect a change in Terraform state. To fix this issue, resync the Terraform state or upgrade the version of your Terraform Cloudflare provider to version 4.44.0 ↗ or later.
Security Events pagination
Fixed an issue with pagination in Security Events' sampled logs where some pages were missing data. Also removed the total count from the events log as these are only sampled logs.
New table in Security Analytics and Security Events
Switched to a new, more responsive table in Security Analytics and Security Events.
Fixed occasional attack score mismatches
Fixed an issue causing score mismatches between the global WAF attack score and subscores. In certain cases, subscores were higher (not an attack) than expected while the global attack score was lower than expected (attack), leading to false positives.
Improved detection capabilities
WAF attack score now automatically detects and decodes Base64 and JavaScript (Unicode escape sequences) in HTTP requests. This update is available for all customers with access to WAF attack score (Business customers with access to a single field and Enterprise customers).
For preview WAF updates, refer to the historical changelog (2024).
Was this helpful?
- Resources
- API
- New to Cloudflare?
- Products
- Sponsorships
- Open Source
- Support
- Help Center
- System Status
- Compliance
- GDPR
- Company
- cloudflare.com
- Our team
- Careers
- © 2025 Cloudflare, Inc.
- Privacy Policy
- Terms of Use
- Report Security Issues
- Trademark